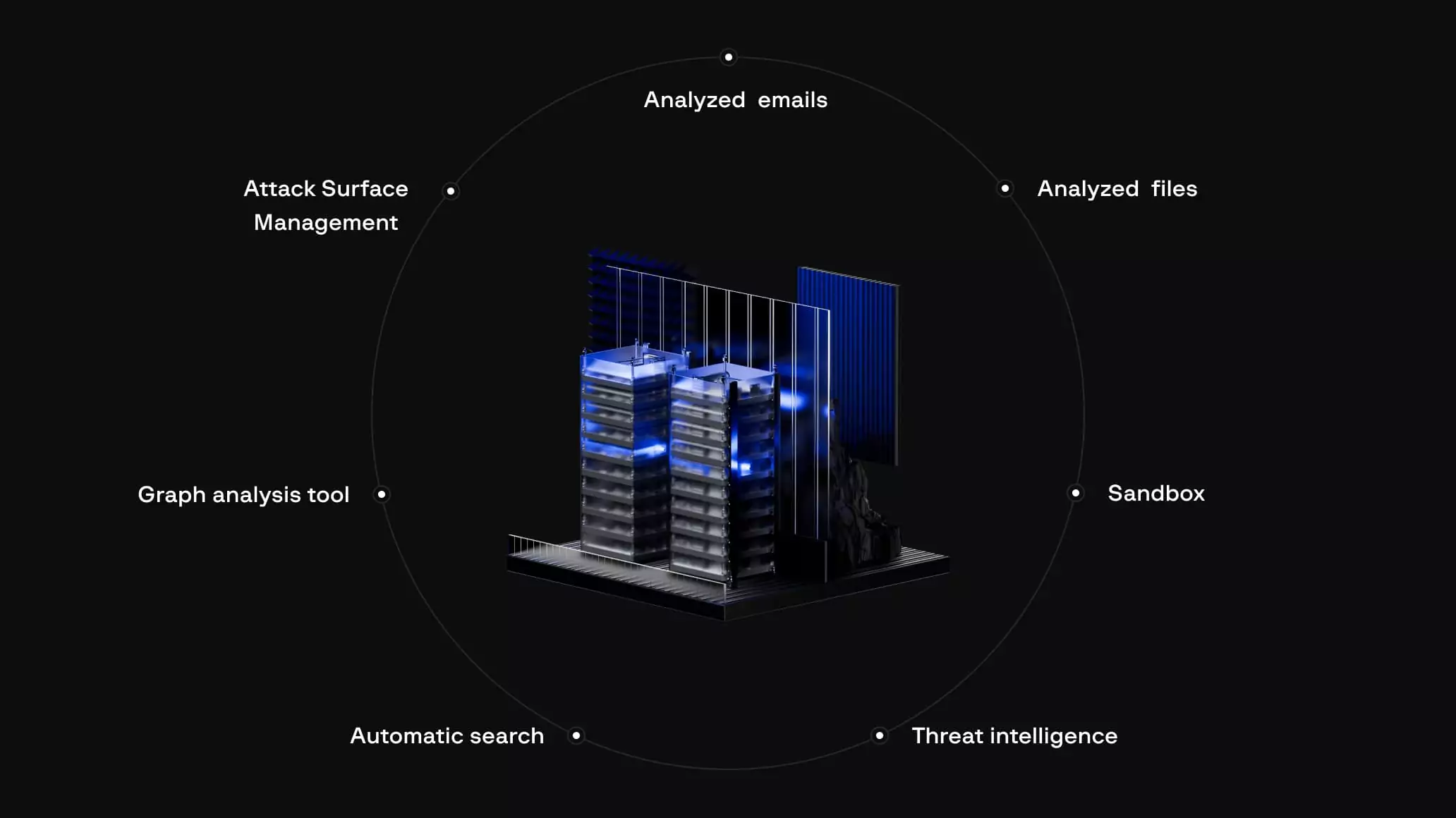
Keep track of your organization’s email security in real time with a customizable dashboard, or explore in-depth insights through advanced analytics
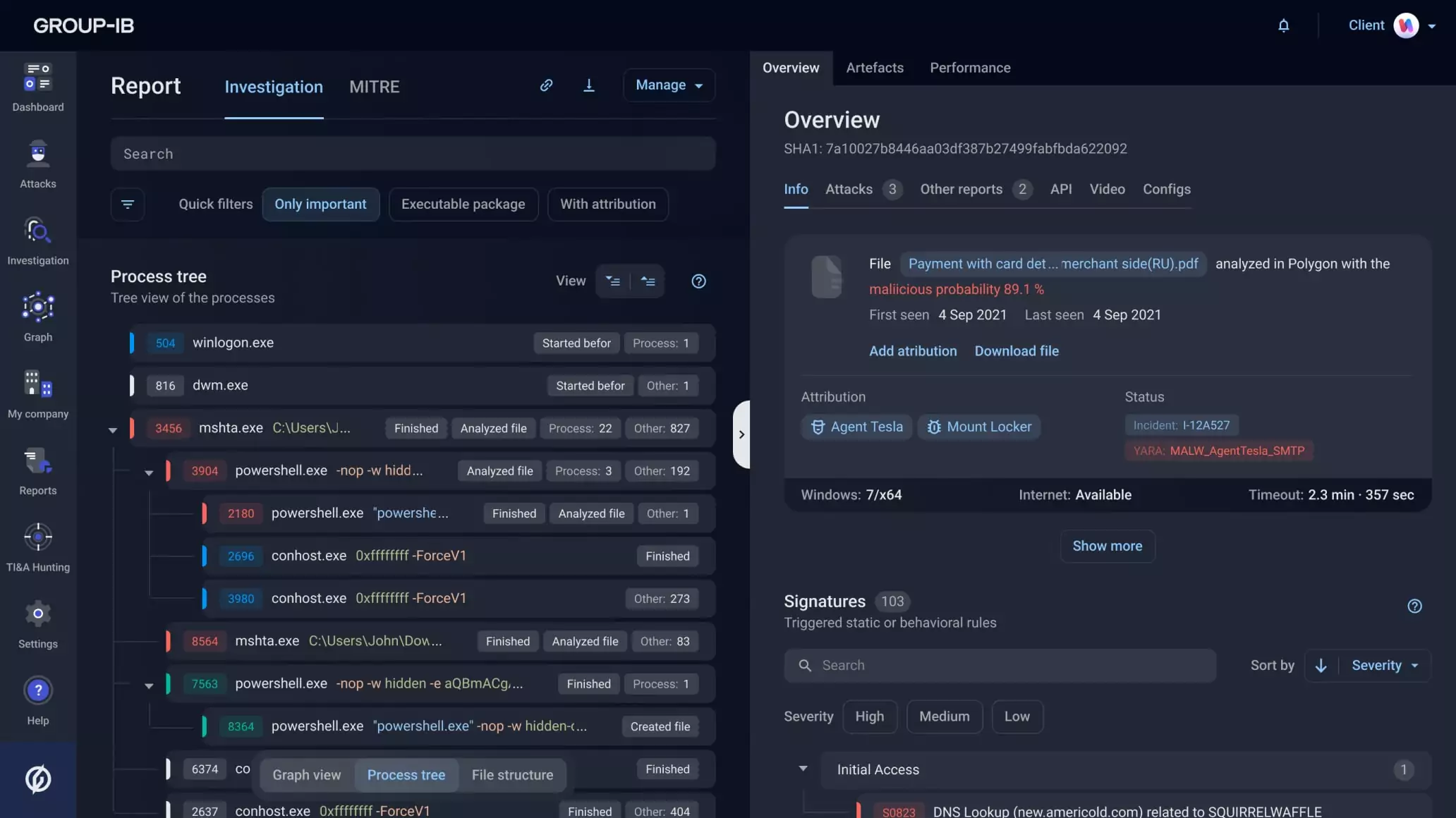
Business Email Protection automatically blocks scams, phishing, malicious files, BEC, ATO, and other threats. With retroactive analysis, it can reclassify malicious objects or URLs and remove them from mailboxes even after delivery
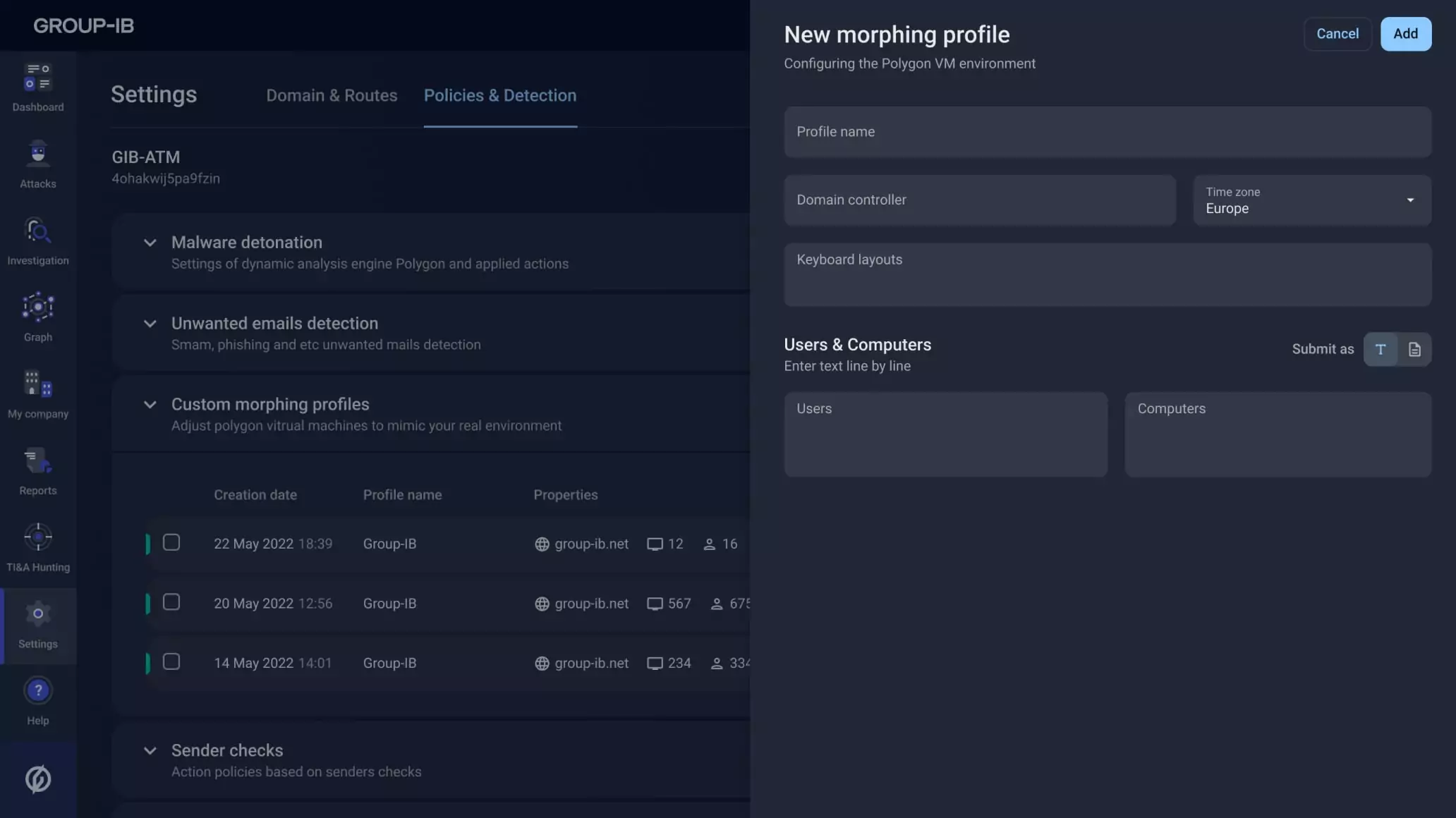
Email-delivered malware often uses evasion techniques to detect generic sandbox environments. Business Email Protection lets you customize the detonation environment to match your organization—language, traffic, usernames, and more—to uncover advanced threats.
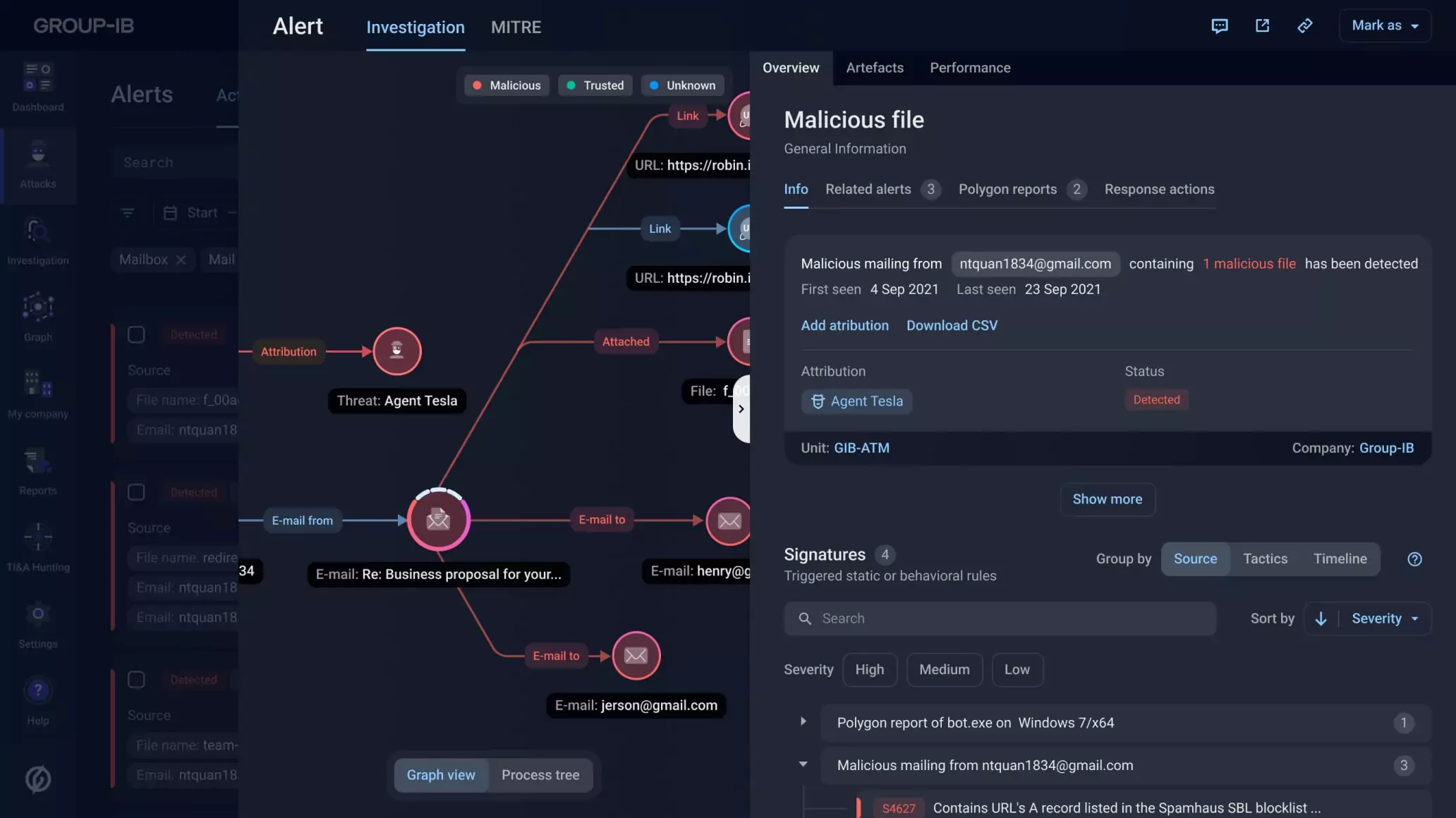
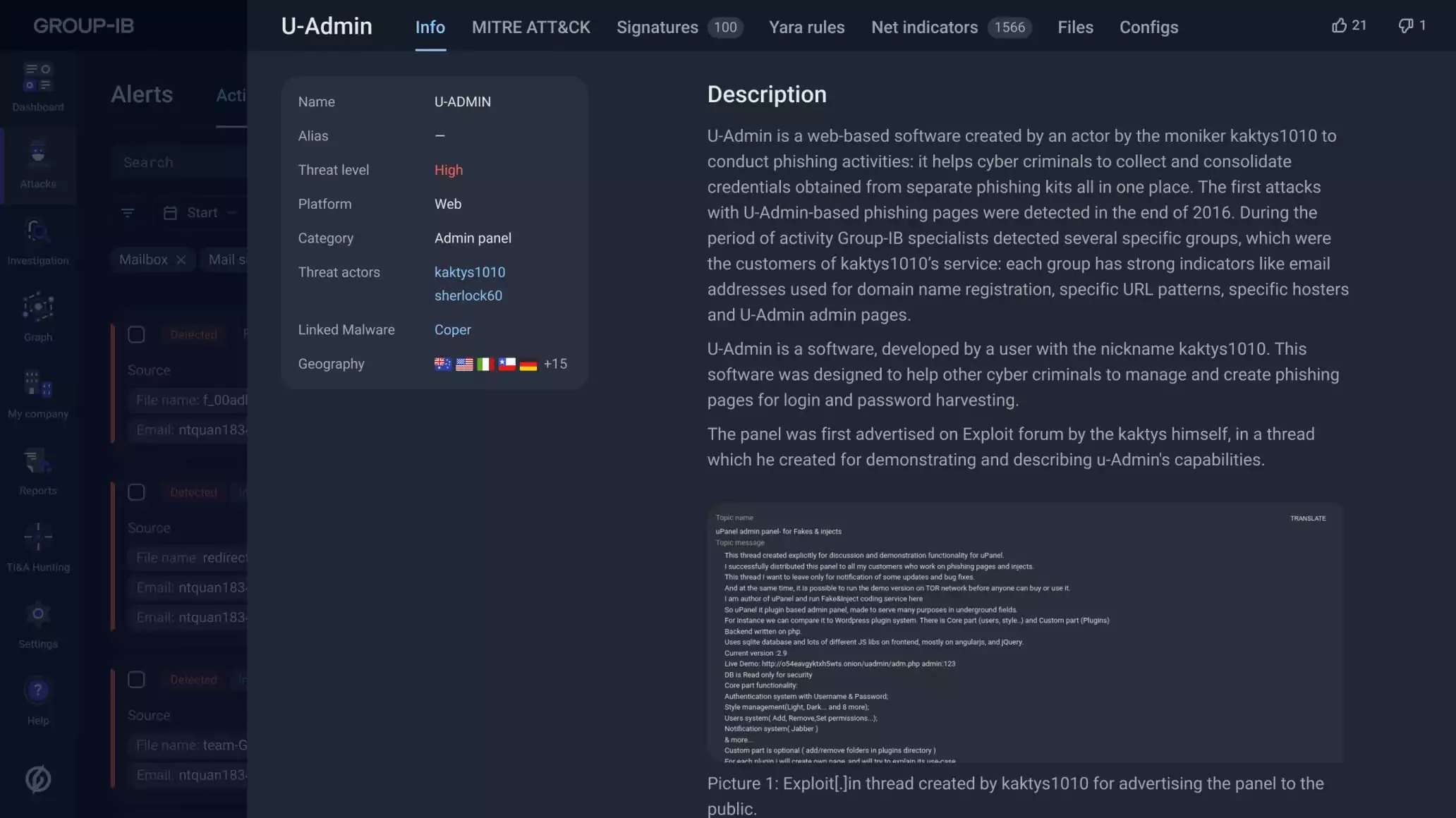
Identify the threat actors targeting your organization with malicious emails and implement defenses to counter them with comprehensive intelligence about their tactics, techniques and procedures (TTPs), network and file indicators of compromise, YARA rules and more powered by Group-IB Threat Intelligence Platform
Hunt for threats in your environment using the information about attacks extracted from emails by Business Email Protection. Analysts can use the Group-IB unified XDR console streamline hypothesis testing, allowing them to identify and remove threats within your network before they cause damage